The Bravo November Numbers Station HOWTO!
Ever wondered how to encode or decode text just like your favorite spy station? Read on.
A while back, a page was linked from the Enigma2000 mailing list, containing instructions from the CIA! It’s in German, but the section describing the encode/decode is pretty easily understood.
First, you get yourself some random numbers, and stick them in five digit groups. This group of random numbers must be at least as long as any encoded transmission you intend to send out.
Second, find a means of securely getting this list of random numbers to the recipient of your message. Historically, everything from sheets of paper to chewing gum have been used for this purpose. For the sake of security, this should be easily concealed, and easily destroyed once used.
Third, compose your message and use a substitution cipher to translate it into numbers. Here’s what the CIA apparently used:
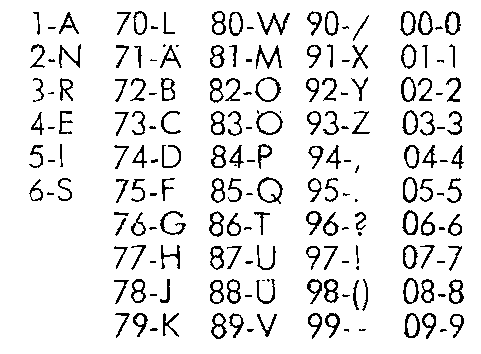
(It’s kinda blurred, but the characters for 71, 83, and 88 have umulats.)
Note that the most commonly used letters are encoded to a single digit to save transmission time… clever.
Also note that this nutty thing has no apparent support for spaces, nor need for such…? If desired, one could probably do something like map A umulat to space. In fact, it would be better if you did not use the CIA’s code as a base, but created your own, for security reasons. I’m just using it as an example here.
Here’s an example message:
W e a r e t h e r o b o t s . 80 4 1 3 4 86 77 4 3 82 72 82 86 6 95
Next, we put it in 5 figure groups. 5 figure groups are not required, but all the cool kids are doing it that way. The CIA Count Control transmissions used to use 4FG’s. I’m using - as a filler to pad it up to a full group at the end.
80413 48677 43827 28286 69599
Well, that’s fine and dandy, but anyone who knows your substition cipher will be able to decipher your message, and that can be determined through fairly simple cryptanalysis. Now, we’re going to use a ‘one time pad’ to ensure that the message will be worthless to anyone who doesn’t have the key to decrypt it!
Still got those random numbers I told you to prepare? Ok, good. Here’s where we’ll use them. We’ll be adding digits of the random number list to the message to (reversibly) scramble it.
The adddition method has one quirk to it: in adding the digits, it will be possible to exceed 10. If you go over 10, just use the last digit of the result. For instance, 8 + 5 = 3.
Here’s our test message and some random numbers:
80413 48677 43827 28286 69599 < - Message 23455 92325 85678 23467 75887 <- One Time Pad 03868 30992 28495 41643 34376 <- Encrypted Sum
Now, find some creative and interesting way to transmit that encrypted sum…
Decrypting the message is the reverse of encrypting it. Get out your code sheet, and write down the recieved message. If you go below 0 in subtracting the one time pad digit from the message digit, plunk a 1 before the message digit, then subtract the pad digit and use only the ones digit…
03868 30992 28495 41643 34376 < - Encrypted message 23455 92325 85678 23467 75887 <- One Time Pad 80413 48677 43827 28286 69599 <- Decrypted Message 80 4 1 3 4 86 77 4 3 82 72 82 86 6 95 99 W E A R E T H E R O B O T S . -
I hope you like text without spaces. *g*
According to the CIA document, this is how the transmission would be formatted:
‘Message characteristic’ (repeat 3x), Group count, Line Number, message start tones, message.
Message characteristic is what SystranBox seemed to call the first element of the callup. It seems to be a serial number; hearing the same three digits here as in a previous message indicates the previous message will be repeated.
Group count is the number of 5 figure groups that will be contained in the message. Simple as that.
Line number indicates where to start on your page of random numbers to find the message key. It corresponds to the first 5 digit block on that line. Of course, the actual code is to be used starting AFTER that block… otherwise you’ve just given a bit of your message. Don’t do that!
Of course, different agencies have used this differently. The MI5 seems to just transmit the line number in the ‘Lincolnshire Poacher’ interval signal sequence. German intelligence would not send a line number, but would send a number identifying a particular agent to let them know to listen up. (Examples: Papa November, DFD21, other ‘2 letter’ stations). Cuba’s intelligence agency (Cuban government intelligence? Surely I jest … um… hi!) sends three 5-figure groups; one seems to contain digits that count off how many times a message has been resent, with the rest possibly being a key used by the computer software their field agents use to decode the transmission.
How you do this is up to you. Sending a line number is optional, but may make it more difficult for someone to decode your transmission if they somehow discover part of a one-time pad. Of course, never re-use your one time pads, and ensure that your agents securely destroy any one-time pads and decoded messages after use.
Voila… you’re cold war awesome!
July 26th, 2006 at 1014Z
“Also note that this nutty thing has no apparent support for spaces, nor need for such…? If desired, one could probably do something like map A umulat to space.”
Spaces are the undoing of many a cipher. Give a half-decent cryptanalysist any sort of word delimiter and they will go to town on finding pattern words (some common ones are a, I, there, initiate, am, we, immediately) and break the substitution down.
OTPs make this harder, though not actually as hard as you might think. Patterns can emerge in those, too, though it’s computationally expensive to find them. People don’t come up with distributions as random as they’d like to think (7, 3, 5, and 8 (in that order) occur extremely often, for example, and are a good starting point for brute force), and /dev/urandom on many systems is a sort of fuzzy finite state machine which can be predicted with some degree of accuracy.